1. Create a new project
Let’s create a new folder calledaws-lambda and initialize a new project by
creating lambda_function.py This example uses Makefile, but the scripts can
also be written for Pipenv.
2. Dependencies
We are usingPyJwt for decoding the JWT token in our code. We will install the
package in the zipping stage.
3. Creating the handler function
In this example we will show how to receive a webhook from QStash and verify the signature. First, let’s import everything we need:verify function will handle the actual verification of the signature. The
signature itself is actually a JWT and includes claims about
the request. See here.
4. Create a Lambda function on AWS
Create a new Lambda function from scratch by going to the AWS console. (Make sure you select your desired region) Give it a name and selectPython 3.8 as runtime, then create the function.
Configuration tab:
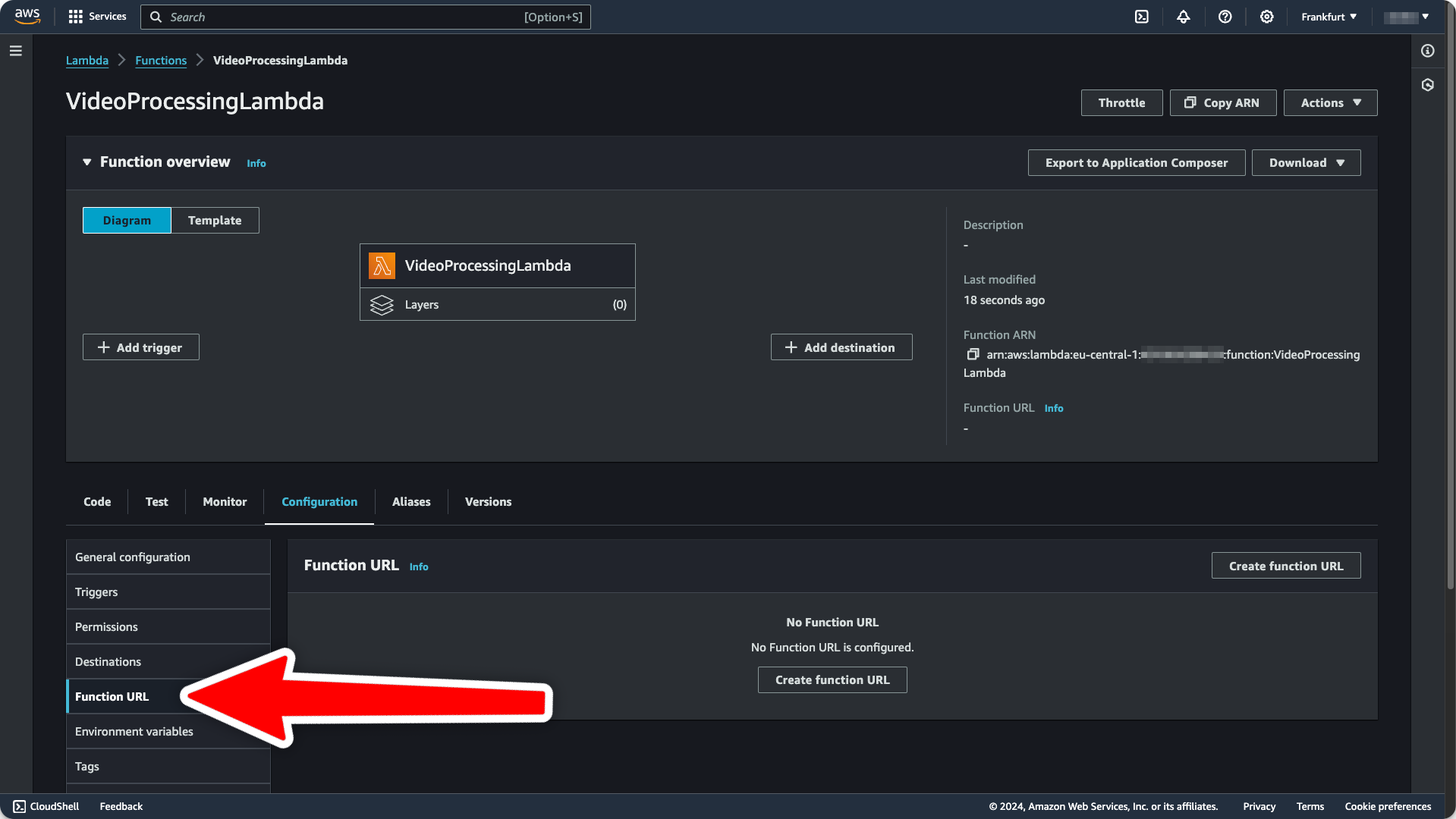
Auth Type = NONE because we are handling authentication ourselves.
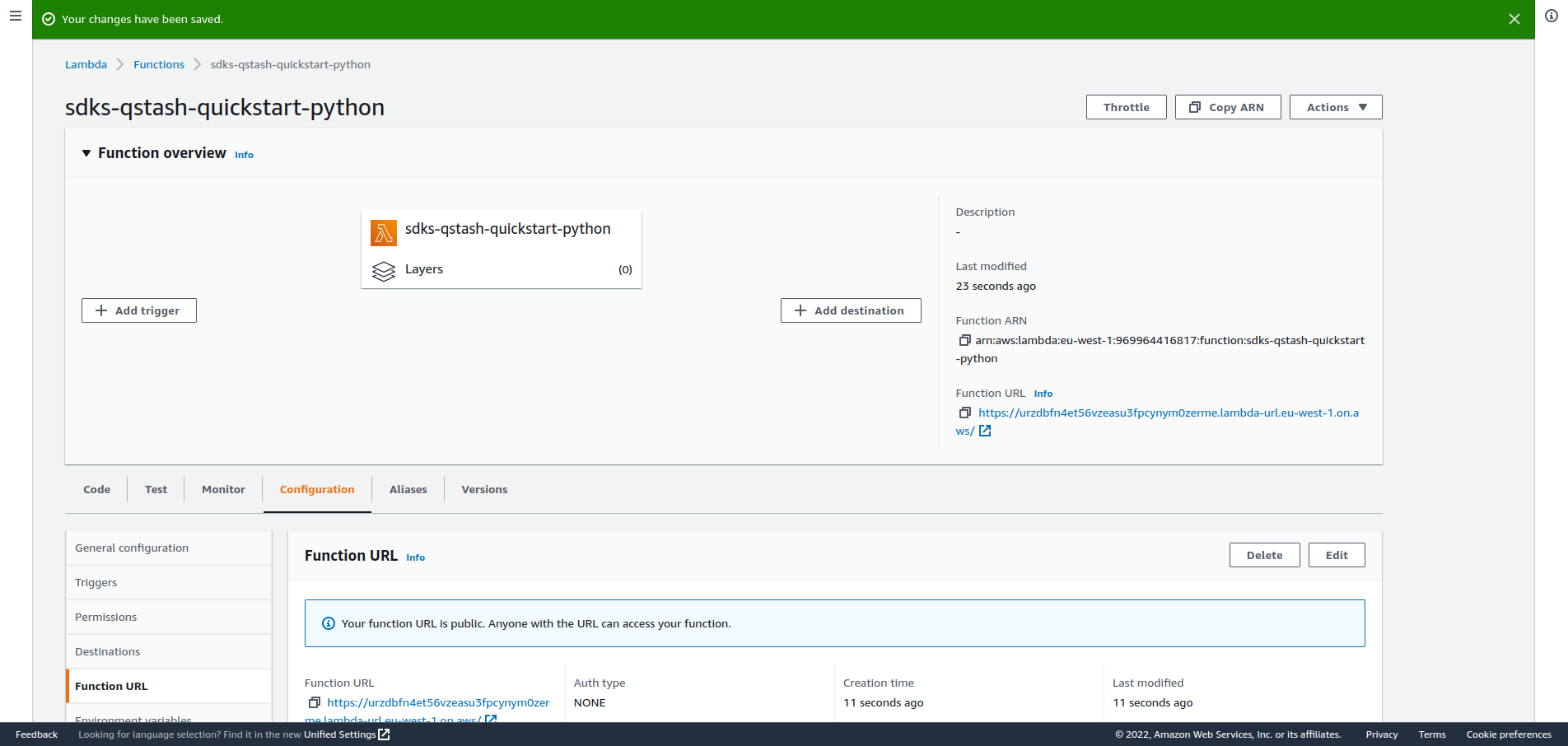
After creating the url, you should see it on the right side of the overview of
your function:
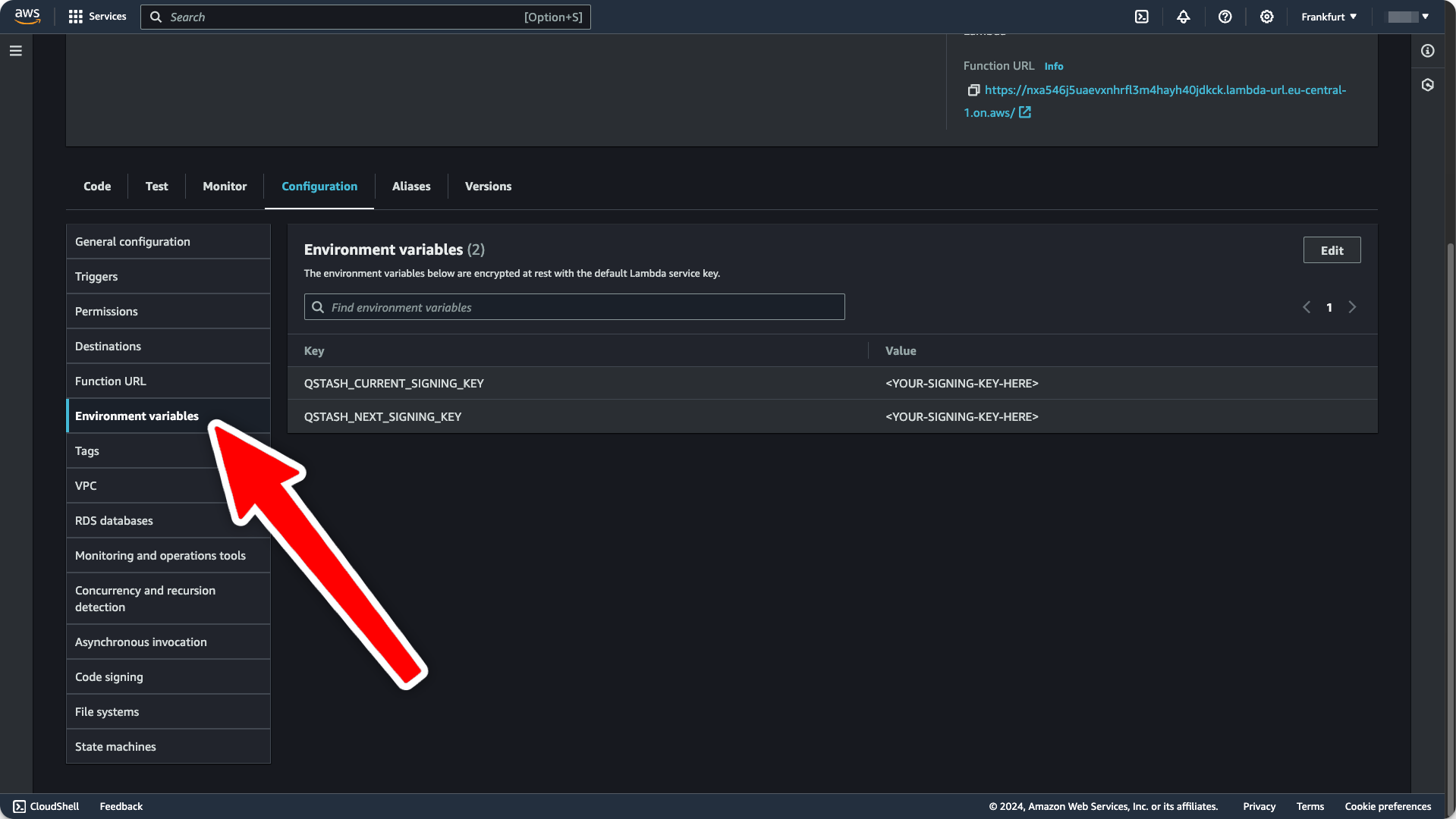
5. Set Environment Variables
Get your current and next signing key from the Upstash Console On the sameConfiguration tab from earlier, we will now set the required
environment variables:
6. Deploy your Lambda function
We need to bundle our code and zip it to deploy it to AWS. Add the following script to yourMakefile file (or corresponding pipenv
script):
make zip this will install PyJwt and zip the code.
Afterwards we can click the Upload from button in the lower right corner and
deploy the code to AWS. Select lambda.zip as upload file.